Over the weekend, Xavier posted about another image with a payload: “More Steganography!”.
Xavier did a static analysis, and I want to explain how you can decode the payload if you opted for a dynamic analysis.
During your dynamic analysis, you will notice the download of a JPEG image from hxxps://zynova[.]kesug[.]com/new_image.jpg.
You can use my tool jpegdump.py to analyze this file:
You can see that data is appended (after EOI, End Of Image). Notice *trailing*.
This can be selected:
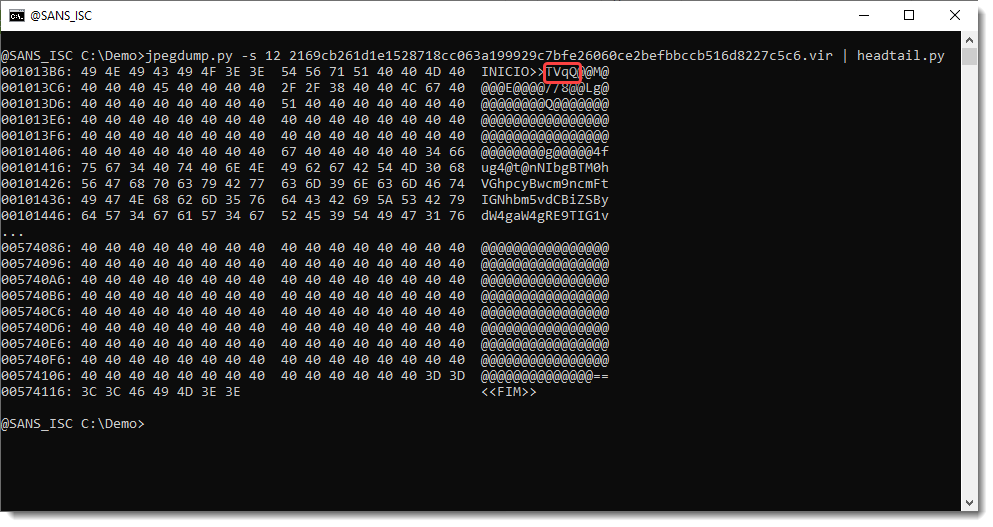
Notice the TVqQ that Xavier pointed out. That’s BASE64 encoding of MZ, the magic header of a PE file.
But the @ character is unexpected. That’s not part of the BASE64 standard. So let’s do some statistics with byte-stats.py:
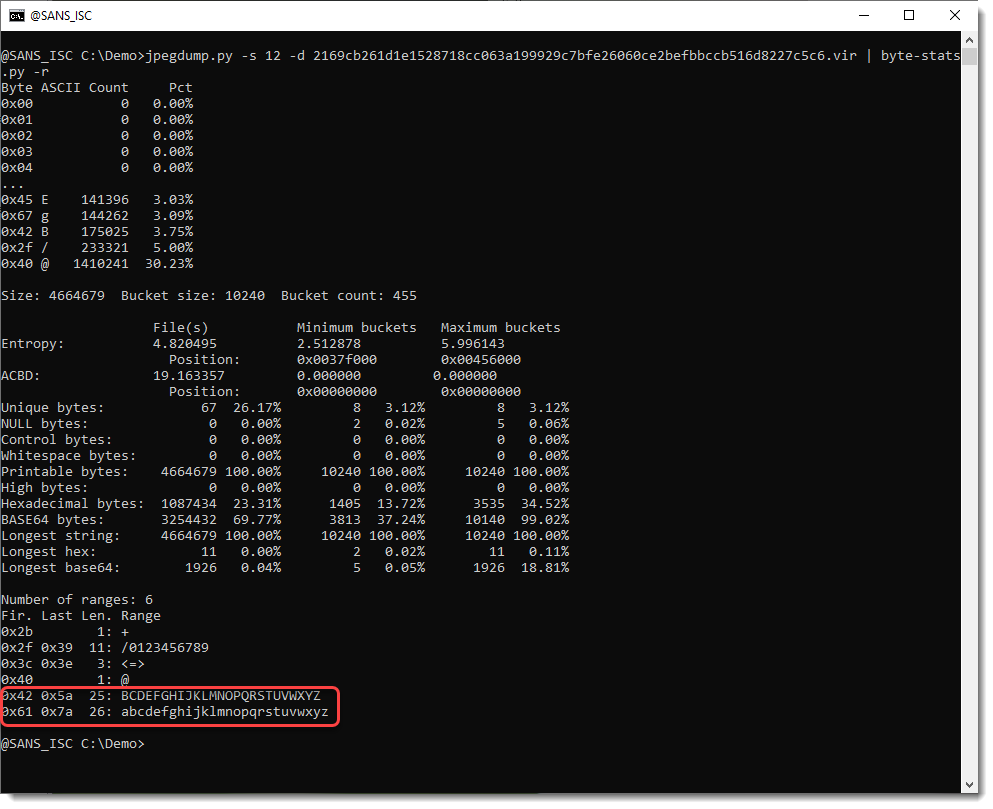
So we see that all the letters appears in this payload, except for letter A. Let’s try out an hypothesis: character @ is a substitute for character A.
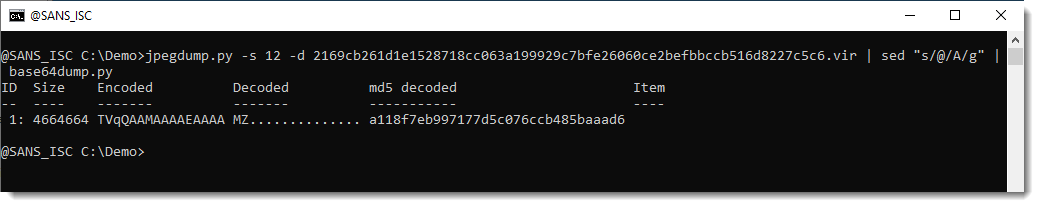
That’s indeed the case, base64dump.py finds a huge BASE64 string, that once decoded starts with MZ.
If you want to see the SHA256 hash in stead of the MD5 hash, so that we can compare it with what Xavier published, you can set environment variable DSS_DEFAULT_HASH_ALGORITHMS.
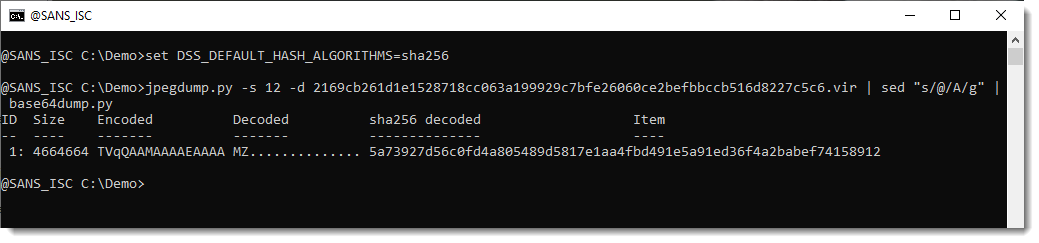
And that’s the same hash as Xavier published for the .NET DLL.
Didier Stevens
Senior handler
blog.DidierStevens.com
